In this blog article, our colleague, Mircea Borcan, Network Security Engineer, talks about the benefits of migrating from traditional WAN to SD-WAN architecture.

Not long ago, networking pioneers were sketching the “Stone Age” features of networking, defining concepts such as Spanning Tree Protocol and VLAN. As the world is in a continuous evolution, it didn’t take long to transition to the “Bronze Age,” with skilled engineers earning the title of “IP Magicians” because they mastered routing protocols and designed networks over long geographic distances (WAN). Networks became larger and made Internet and Intranet services within companies increasingly sought after. This raises the issue of scalability in terms of network management operations and, of course, the security of these networks.
Networking is transitioning along with these needs towards the “Renaissance and Programmability” eras. Concepts such as centralized controllers, plan separation, programmability, and underlay versus overlay emerge. Nowadays, we find ourselves at the boundary between these two eras, and from the perspective of WAN networks, this translates into incorporating software mechanisms into the networking realm. This is where we discuss Software Defined Wide Area Network (SDWAN) solutions.
Cisco’s solution for SDWAN was born in 2017 with the acquisition of the company Viptela. Viptela’s technology was integrated into the state-of-the-art routing solutions already existing in Cisco’s portfolio, shaping a new generation of WAN networks based on the concept of “intuitive networks,” networks that constantly adapt to traffic conditions, provide automation capabilities, and natively incorporate the necessary security mechanisms in the current cyber climate.
Historically, the most scalable WAN architecture was represented by the implementation of DMVPN technology. The management mechanisms required connecting to each device individually and tying administrators to the command line, highlighting the need for centralization, a process that enables managing the entire infrastructure. In SDWAN, management is achieved through a so-called “Single Pane of Glass,” a centralized console where new features can be configured and all data about the managed devices can be viewed, enhancing the troubleshooting process.
In troubleshooting, engineers often face application functionality issues. In the transport area, which is usually provided by a service provider, parameters such as delay, jitter (variation in delay), and packet loss (latency, jitter, and loss) may change. Cisco’s solution takes these parameters into account to dynamically alter packet routing. For applications sensitive to delays (e.g., VoIP, Video), if one of the WAN links fails to meet the required parameters, the traffic for that application will be automatically rerouted through another WAN connection. In the ideal scenario where all WAN connections meet the required parameters, traffic will be load balanced across all circuits, also done automatically without administrator intervention.
If one of the WAN circuits is an Internet circuit, SDWAN offers the possibility of connecting users locally from that location directly to the public network, eliminating the need to route traffic through SDWAN tunnels to a centralized Internet exit. This preserves the bandwidth of the circuit, and the network user experience is generally more satisfactory. Of course, the Internet circuit is also used for the SDWAN area, but it only routes private IP classes to other locations. Local Internet traffic can be secured by incorporating Cloud Security solutions, which provide various protection mechanisms such as Web Proxy or DNS Filtering. When the SDWAN area with local Internet access intersects with traffic security solutions delivered from the cloud, the concept known as Secure Access Service Edge (SASE) is formed, aiding in accelerating digital transformation through service convergence.
The scalability of SDWAN network configurations comes from leveraging the concept of Plug-and-Play, which translates to centralized configuration that is distributed to routers when they connect to the network. In fact, the configuration present at the central level is segregated into templates, allowing the reuse of a single configuration on multiple devices, improving traceability and troubleshooting processes.
From an architectural perspective, the SDWAN solution can be seen as a “fabric” within which there are multiple separate roles for each type of device. These functions are mapped to the planes within a router that is part of a classic network – management, control, and data. In SDWAN, the only plane under the jurisdiction of the router is the data plane. Thus, the interesting traffic between two locations served by different routers will traverse the data planes of the two devices. In terms of routing, the routing tables of the devices are populated using the control plane through the vSmart controller. It aggregates routing updates from all devices in the network and transmits them to the other routers. vSmart can be seen as the counterpart of a route reflector in the BGP protocol. Infrastructure management is carried out through the vManage controller, achieving the third plane, namely the management plane within the fabric. The last plane is the orchestration plane, which ensures the initial onboarding of routers into the fabric and is provided by the vBond controller.
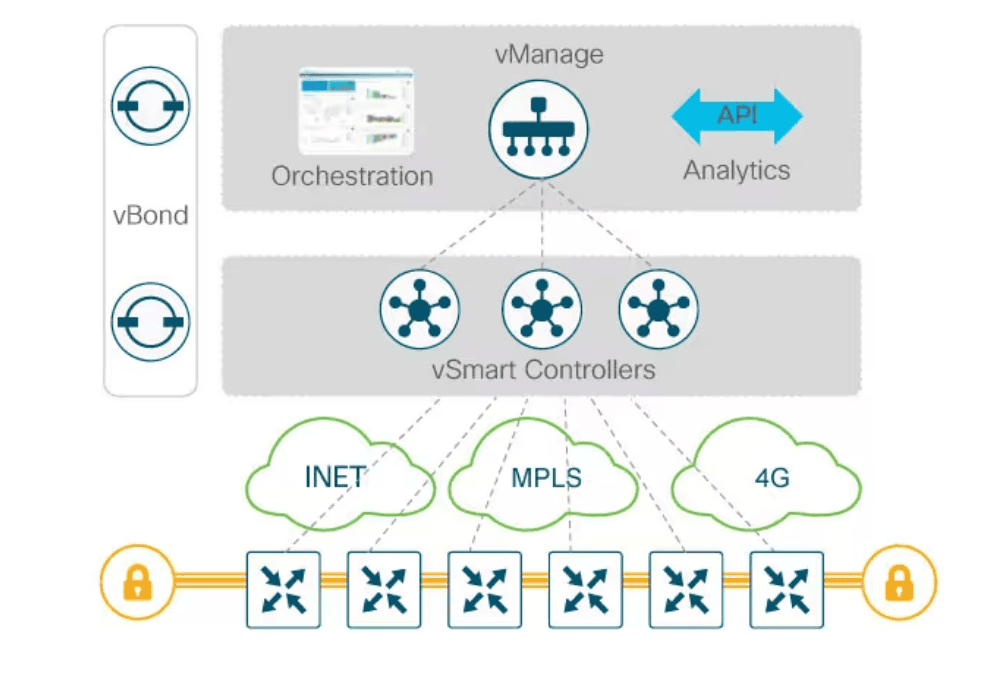
Security is generally a subject that must be treated with utmost responsibility. The principle of “layered security” is successfully applied in SDWAN, outlining three directions of interest within the fabric. In the initial phase, as mentioned earlier, the enrollment of routers into the SDWAN fabric is done through vBond, using a whitelisting model that enrolls only devices whose serial numbers and digital certificates correspond to the preloaded list provided by the administrator. The connection is initiated from the routers to vBond, which verifies the serial number and data from the certificate presented by the router, and then validates the equipment’s request to enter the fabric. In the data plane, the traffic between routers is natively secured using the IPSEC protocol, protecting the useful data transmitted through the fabric. The third layer of security is represented by securing the traffic in the management and control planes using protocols such as DTLS or TLS.
Considering the architectural and operational complexity of today’s networks, as well as the need to secure data and communication infrastructure, Cisco’s SDWAN solution manages to provide simplicity in configuration and management while adhering to industry best practices in terms of cybersecurity.