Second part of a 2-part blog post, written by Mihai Dumitru, Chief Architect at Arctic Stream, about a Multicloud IT infrastructure, integrating Cisco SD-WAN, AWS and Azure.

Extending the Cisco SD-WAN to AWS
The Cisco SD-WAN provides a secure cloud scale architecture designed to meet the complex needs of modern WANs through three key areas: advanced application optimization, multi-layered security, and cloud integration.
Interconnection of Cisco SD-WAN and AWS Transit Gateway brings the following benefits:
- Automated and easy connectivity provisioning to the most optimal AWS entry point for the customer’s data center, branch, and hub locations.
- Application and data telemetry in and out of AWS for reporting/chargeback.
- Dynamic routing, multiple path selection, and deterministic failover behavior through the use of Cisco’s proprietary Overlay Management Protocol (OMP) and SD-WAN Secure Extensible Network (SEN) policies.
- Regional hubs interconnecting multiple AWS Transit Gateways and AWS regions via SEN.
- Scaling virtual private network (VPN) bandwidth from 1.2Gbps up to 50Gbps using Equal Cost Multi Path (ECMP).
With AWS Transit Gateway, there’s no need for a transit VPC to terminate multiple VPN connections from vEdge cloud virtual routers in SD-WAN VPC to VGW in each spoke VPC.
In doing so, branches connect through the AWS backbone, as well as connect with AWS workloads.
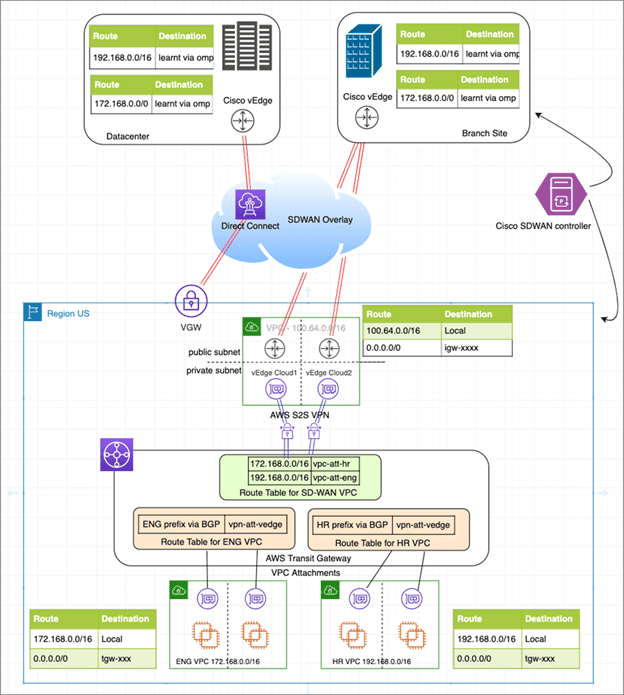
Connecting Branch to AWS – SD-WAN VPC, TGW, and VPN Attachment
In the reference architecture, branch vEdge cloud virtual routers terminate proprietary secure Cisco SD-WAN tunnels from the branch over the internet or via AWS Direct Connect from the data center to a pair of vEdge cloud routers in an SD-WAN VPC on AWS. The vEdge cloud routers terminate standard IPSec VPN tunnels from SD-WAN routers to AWS Transit Gateway as VPN attachments.
The diagram below shows an example. In this example, there are two additional application VPCs attached to AWS Transit Gateway. The branch/data center can talk to the application VPC workloads, but VPC workloads should not talk to each other. This is a segmentation use case.
To achieve the desired connectivity, three different route tables have been configured on the AWS Transit Gateway. Route table1 is associated with one application VPC; route table2 is associated with the other VPC, and route table3 is associated as a VPN attachment with the SD-WAN VPC.
The IP routes in the AWS Transit Gateway route tables associated with the application VPCs are learned from the SD-WAN VPC using route propagation. The routes in the route table associated with the SD-WAN VPC are propagated statically.
Additionally, a static route is configured on the VPC route table for each application VPC with tgw-xxxx as the next hop for non-local routes. Similarly, a static default route is configured on the SD-WAN VPC route table that points to igw-xxxx.
The routes between the SD-WAN VPC and the branch are learned via Cisco’s SD-WAN OMP. By redistributing BGP routes into OMP, the SD-WAN network becomes aware of the AWS infrastructure. Traditional route filtering options like route maps can be used in order to make redistribution more granular.
Putting Them All Together
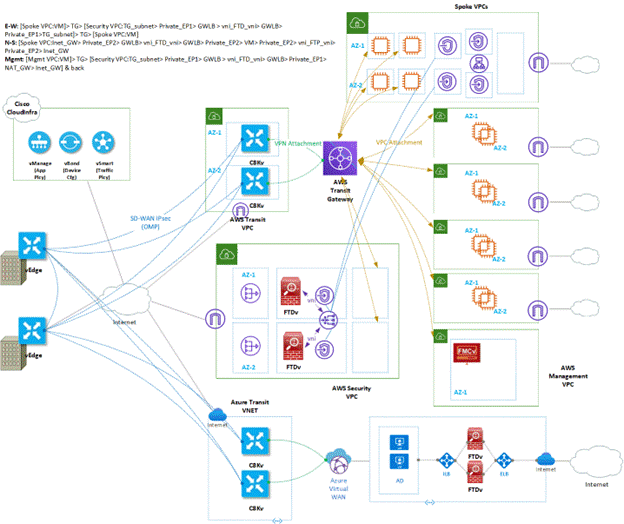
The diagram below summarizes the above-mentioned architecture concepts, as they were put in production.
The AWS Transit Gateway, the AWS Transit VPC and the entire SD-WAN network have been deployed automatically with the Cisco vManage. From there, the AWS Transit Gateway has been extended to the pre-existing AWS Spoke (application) VPCs. An additional Security VPC, hosting Cisco FTDv firewalls, has been added manually for E-W and N-S inspection. Yet another VPC has been created for various network security appliances (especially firewall management).
At the same time, the Cisco SD-WAN has been also extended to Azure, where the AD resides.
Sources:
- https://aws.amazon.com/blogs/networking-and-content-delivery/design-your-firewall-deployment-for-internet-ingress-traffic-flows/
- https://aws.amazon.com/blogs/networking-and-content-delivery/scaling-network-traffic-inspection-using-aws-gateway-load-balancer/
- https://aws.amazon.com/blogs/networking-and-content-delivery/integrate-your-custom-logic-or-appliance-with-aws-gateway-load-balancer/
- https://aws.amazon.com/blogs/networking-and-content-delivery/best-practices-for-deploying-gateway-load-balancer/
- https://aws.amazon.com/blogs/networking-and-content-delivery/introducing-aws-gateway-load-balancer-supported-architecture-patterns/
- https://aws.amazon.com/blogs/networking-and-content-delivery/centralized-inspection-architecture-with-aws-gateway-load-balancer-and-aws-transit-gateway/
- https://aws.amazon.com/blogs/apn/centralized-traffic-inspection-with-gateway-load-balancer-on-aws/