In this article, our colleague Alexandra Marcu, Junior Engineer, explains the importance of the firewall in protecting networks and data against cyberattacks. Alexandra details how firewalls work, the available types, and how they contribute to maintaining security
in an increasingly vulnerable digital world.

Imagine one day you connect to your company’s network and discover that sensitive data has been compromised. It all started with a single unsecured file that slipped through the network’s “shields”. This is a daily reality for many organizations. However, with a well-configured firewall, such scenarios can be prevented.
Your shield in the digital world
The firewall is an essential concept in the field of cybersecurity. Its necessity arose with the growing use of computer networks and the Internet, along with the increasing dangers to which users were exposed. Highly sensitive transmitted data was easily compromised. The CIA triad (Confidentiality, Integrity, Availability) describes the ways attackers can endanger information transmitted between users. Data must be confidential, meaning accessible only to the intended users, intact without being altered by third parties, and always available when needed. The firewall is one of the solutions used to protect the attributes described by CIA, in combination with other technologies.
How does a firewall work?
A firewall is a network device that acts between a company’s local network and the Internet. It functions as a “barrier,” monitoring and controlling network traffic based on predefined rules set by the network administrator. The firewall examines incoming packets to the local network and decides whether they meet the criteria to be transmitted further. The rules can be simple, such as blocking access to certain geographic locations, or very complex, analyzing traffic types, ports, applications, and their behavior.
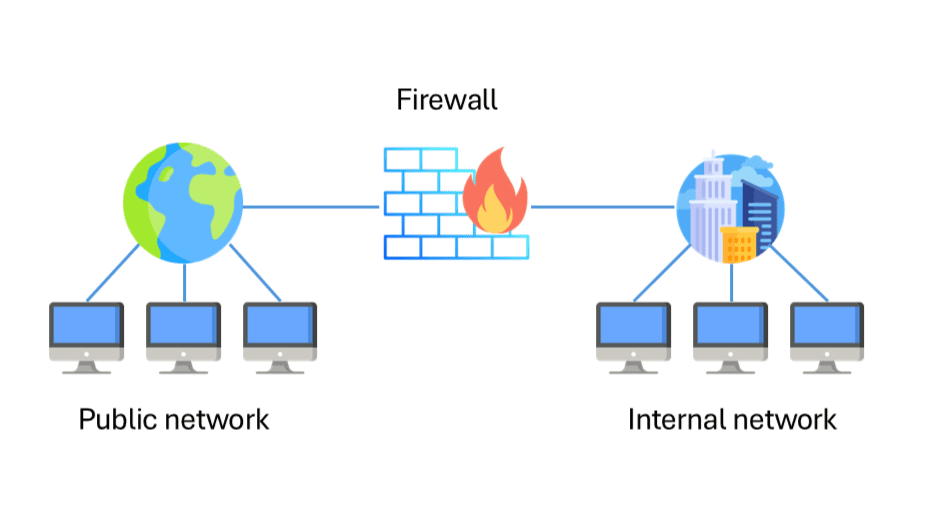
In addition to basic functions, a firewall can detect unusual traffic patterns, such as a large volume of data transmitted in a short period. It can recognize attack types, the most common being DoS (Denial-of-Service) or DDoS (Distributed Denial-of-Service), which compromise network equipment with false traffic, or Man-in-the-Middle attacks, where the attacker intercepts and even alters communication. After identifying abnormal behavior, the firewall can block suspicious data packets or restrict access to certain IP addresses, ports, and/or applications.
Types of firewalls and uses
The firewall has evolved significantly over the decades. In the ’90s, it started as a simplistic device that only filtered transmitted packets based on rudimentary rules and monitored network traffic. Today, it offers many more functionalities and implementation possibilities, as described below.
The Next Generation Firewall operates at the application level, having evolved to face complex threats. Documentation highlights its most important capabilities: standard firewall features like Stateful Inspection, intrusion prevention (IPS – Intrusion Prevention System), Application Awareness and Control, and integration with intelligent sources updated with information on potential new attacks. These allow the firewall to detect and block cyberattacks in real-time and adapt to new threats through future upgrades. This device can be implemented in the following ways:
- Hardware Firewalls: usually installed at the boundary between the local network and the Internet, thus protecting the entire network from external attacks;
- Virtual Firewalls: can be implemented in Data Centers as virtualized containers on network equipment, in Cloud infrastructures, and provide protection similar to hardware firewalls.
An important advantage is the segmentation of traffic zones, allowing the firewall to protect different parts of a network according to needs. The most common zones are:
- External zone: the Internet;
- Internal zone: the local network of an organization, where internal devices and resources are located;
- Demilitarized zone (DMZ): a buffer zone between the internal and external networks, where servers accessible both from inside and outside the network are placed.
Traffic between these zones is usually controlled by a set of rules specifying the types of allowed or denied traffic, translating private IP addresses into public IP addresses, and permitting secure connections through a virtual private network (VPN).
In terms of implementation, the most common modes are Transparent and Routed. A firewall in Routed mode is responsible for separating network segments, routing traffic between them, and granular traffic control. In Transparent mode, the device does not modify the routing scheme, only handling traffic filtering. This method is widely used since it does not require modifying the existing infrastructure—securing the network can be achieved by simply adding the firewall device, functioning as a “bump in the wire.”
To ensure optimal protection against cyber threats, security policies must be periodically updated during maintenance processes. These updates are necessary to improve existing security measures to meet the latest market requirements.
Despite the emergence of other security solutions, the firewall remains a fundamental element that must exist in clients’ networks. It acts as the first line of defense, much like walls were built around fortresses in the past. For a higher level of protection, besides using a firewall, it is recommended to use security solutions at the Endpoint, Web, E-mail levels etc.
Firewall in the current context
Cyberattacks are becoming increasingly sophisticated and harder to detect, making them implicitly harder to stop. In this context, the firewall plays a crucial role in protecting personal data, sensitive information, and critical resources. It is an active component that helps safeguard the integrity and confidentiality of data while ensuring controlled access for authorized users.
For example, the latest Secure Firewall Threat Defense 7.6 version from Cisco brings new features to keep pace with emerging threats. In terms of Cloud integration, new capabilities such as Cisco Security Cloud Integration and AI Assistant have been added. The Threat and Malware category benefits from the introduction of SnortML for detecting known attacks as well as zero-day threats (exploiting unknown vulnerabilities), while Simplified Do-Not-Decrypt allows users to choose which connections outside the local network should not be decrypted. The SD-WAN solution also benefits from expanded capabilities with SD-WAN Wizard, which introduces a simplified and automated way to create, configure, and manage topology in FMC (Firewall Management Center).
In an ever evolving and increasingly connected digital world, using a firewall in a local network is no longer optional but a necessity. Firewall solutions can be customized to meet client needs and implementation possibilities. Arctic Stream positions itself as a trusted partner in this process, with a team of specialists ready to provide consultancy and support.
For more information or to discuss your network’s specific needs, contact us at [email protected] and consult a specialist to ensure you are protected against the latest threats.