In this blog article, our colleague Mircea Borcan, Senior Network Engineer, clearly explains how modern networks can be protected against cyberattacks. From next-generation firewalls and VPN solutions to user best practices and adapted security policies, the article provides a clear overview of the steps any organization must follow to safeguard its IT infrastructure. It serves as a practical guide for companies that want to remain secure, efficient and prepared in the face of digital threats.

As the interconnected world continues to evolve, security risks and concerns must be properly addressed in order to prevent any breach that could cause damage to computer systems. To keep pace with technological advancements, it is necessary to tackle the new threats that emerge in cyberspace today. The increase in the number of attacks over the past decade has become an ever-growing problem, turning into a profitable criminal enterprise. No one can completely avoid becoming a target, but strong security mechanisms can be developed and applied to minimize the risk of being compromised.
Convergent security
- Vicious circle
For a better understanding of the so-called rules of cyberspace, it is simple to take the example of ransomware. Ransomware is malicious software used in a cyberattack to encrypt a victim’s data with an encryption key known only to the attacker, thus making the data unusable until the victim pays a ransom. What happens if a business is infected with malware? The organization often considers that the correct solution is to pay the ransom, as it seems to be the most cost-effective path. In fact, for the purpose of recovering its data, this is indeed the most efficient solution. However, the problem is that any institution that pays directly contributes to financing the empire of malware development. Consequently, well-intentioned institutions become the biggest sponsors of this industry. The more ransoms are paid, the more sophisticated the attacks become. Attacks must be detected and prevented at the moment they occur and stopped if, nevertheless, they manage to reach their target.
- Security artichoke
The security artichoke analogy states that, in order to compromise a network (or to reach the “core” of the artichoke), only certain layers of leaves need to be removed, not all of them. Thus, theoretically, an attacker can peel away the outer leaves and reach the heart of the network. With a focus on security, the network administrator must adopt a layered approach, ensuring that the network will not be compromised even in the unlikely event of the perimeter firewall being breached.
- Perimeter firewall
In order to reduce risks, firewall technology has evolved from the classic Layer 4 firewall to the Next Generation Firewall (NGFW). The use case of a perimeter firewall is illustrated in figure 1.
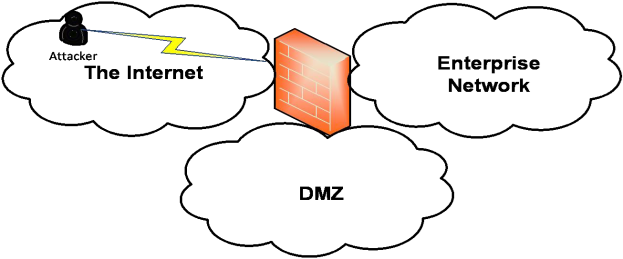
Fig. 1. Perimeter firewall
In addition to the traditional capabilities of a Layer 4 firewall, such as stateful packet inspection, VPN, and NAT, the Next Generation Firewall (NGFW) introduces many other functionalities, including application firewall with advanced packet inspection (in-line deep packet inspection), encrypted traffic inspection, website and application filtering, as well as antivirus protection. The purpose of including these new capabilities is to enable deeper inspection, focused on verifying packet content and comparing malware signatures. NGFW also provides a granular filtering mechanism through the use of application control (app control). With this functionality, the network administrator can decide which parts of a website should be accessible to end users, filtering out unwanted sections (for example, document sharing). Another essential role of the perimeter firewall is the implementation of the security policy for the demilitarized zone (DMZ). The DMZ is used to host services exposed to the external area of the organization, which, in most cases, is the Internet.
- Connecting remote locations
Any medium or large-sized company has certain remote locations that need to access central resources, so these must be connected to the network. The problem is that the organization does not have the physical infrastructure required to reach every remote location. To connect these peripheral sites, an organization has two approaches: the first is the use of leased lines, which can connect the locations to the headquarters. This measure ensures the confidentiality and availability of the network, since these lines would be used exclusively by the respective company. The disadvantage of this configuration is the cost. If an organization has many locations that need to be connected, situated in different geographical areas, then the costs increase exponentially. Another issue associated with the use of leased lines is the inability to provide network access for employees working off-site. The leased line–based solution is illustrated in figure 2.
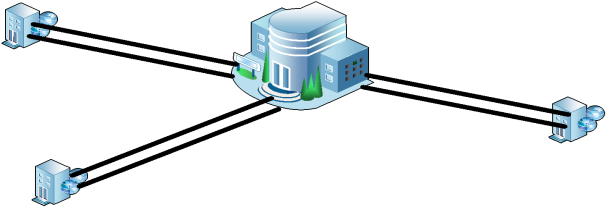
Fig. 2. Connecting remote sites – Leased Lines
The second approach used for connecting remote locations is VPNs (Virtual Private Networks). The concept of VPN removes the boundary between private and public networks. It allows the creation of private networks over existing public networks, such as the Internet or a service provider’s infrastructure. On the one hand, implementing VPNs introduces a certain level of complexity, but on the other hand, it provides mobility — considering that we are in the era of BYOD (“Bring Your Own Device”) — and reduces costs. The use of VPNs ensures the three fundamental concepts that define information security: Confidentiality, Integrity, and Authentication (CIA).
- Confidentiality of information is achieved through the use of encryption algorithms such as AES or 3DES. Encryption is necessary to avoid situations in which a Man-In-The-Middle (MITM) attacker intercepts transmitted information and attempts to reconstruct the original message. Through encryption, even if a MITM can see the packets, they cannot understand their content because they do not possess the encryption key.
- Integrity is ensured through the use of hash functions. The original message is processed with a hash function, and the result is attached to the information to be transmitted. At the destination, a new hash is calculated and compared with the one received. If they are identical, it means the message was not corrupted during transmission; if not, the message is rejected.
- Authentication of the communicating parties is achieved through the use of keyed hashes (HMAC). Since only the correspondents possess these keys, a MITM attack attempting to impersonate someone else cannot succeed. Even if an attacker sends a message pretending to be another party, without the appropriate key they will not be authenticated by the destination and their message will be rejected.
The VPN solution is illustrated in figure 3.
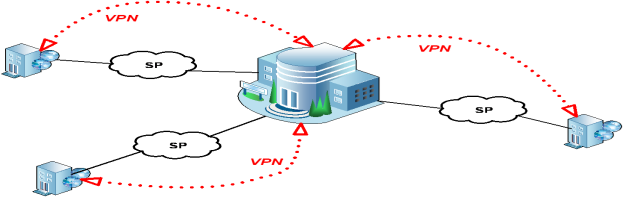
Fig. 3. Connecting remote sites – Virtual Private Network
- End users – the main concern
End users are the consumers of network resources. On the one hand, all applications that are developed and the entire network infrastructure that is built are intended to meet the needs of end users. On the other hand, however, end users represent the most vulnerable and exposed points of the network. To ensure convergent security mechanisms across the entire network, end users must be authenticated by the system. In addition, after authentication, a user should not have access to all resources, but only to those relevant to their activity. In other words, users must be authorized to perform only certain actions. Finally, the actions of each user must be recorded (logged), this process belongs to the concept of accounting.
Beyond the AAA framework (Authentication, Authorization, Accounting), the user must also be evaluated in terms of compliance (postured). An endpoint connected to the network must have the latest antivirus signatures and up-to-date operating system security patches. Compliance evaluation of an endpoint can be carried out by a centralized server. If the endpoint does not comply with the organization’s security policy, the centralized server blocks the device’s access and initiates the update process. After this process is completed, the device is authenticated by the server and granted access to the network. The implementation of such a solution uses protocols such as 802.1X and RADIUS, as illustrated in Figure 4. The switch acts as an intermediary device, with the role of transmitting messages between the client and the server.
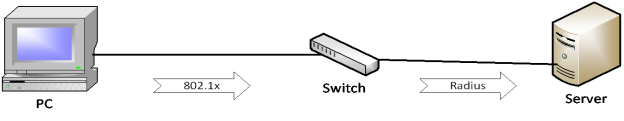
Fig. 4. User authentication
In addition to implementing multiple security measures, a company must also introduce cybersecurity awareness training programs for its employees. To comply with the organization’s security policy, on the one hand, and to understand the dangers present in cyberspace, on the other hand, these training programs must be held periodically and be mandatory for all employees.
In conclusion
To minimize risks in today’s global cyberspace, every company should adopt a layered approach. Defending the network against cyberattacks requires constant vigilance and continuous education. Best practices in network security combine several actions, including regularly updating patches, disabling unused services and ports, using strong passwords, and changing them frequently.
At the macro level, there are many other aspects to consider, such as protecting the company’s public resources, securing WAN networks, and authenticating and monitoring end-user traffic. It is essential that employees are educated about the risks associated with social engineering. Unfortunately, the most common network attacks are caused by insufficiently trained personnel. Therefore, strategies for identity verification via phone, email, or face-to-face must be developed to prevent phishing attacks. In addition, drafting a written security policy is a key element in the process of educating employees.
The methods analyzed in this article represent a convergent mechanism for network security protection and management. Organizations must remain constantly vigilant and defend themselves against evolving threats by developing security policies adapted to the malicious software present in cyberspace. For more information or commercial details, please contact us at: [email protected].