In this article, Mihai Dumitru, Chief Architect, presents the importance of implementing CIS 18 for small and medium-sized organizations. He also outlines the essential steps, explaining how this framework helps protect IT infrastructure without large investments, while addressing common cybersecurity challenges faced by organizations.

Most likely, the majority of our clients have gone through a NIS audit (Network and Information Systems, now in version 2), which is a European Union directive on cybersecurity. The legislation applies to all medium-sized or larger economic entities (10 million euros in revenue or 50 employees) that are providers of essential or important services (energy, utilities and beyond). This article is not for them, if the recommendations they’ve received have already given them enough to do — or it’s also for them, if they need a practical approach to supplement NIS2. It is for companies with up to 50 employees, who are asking themselves “but how are we really doing? The IT department says they know what they’re doing, but do they really?” It is for those who want a practical, common-sense guide at hand, without the high initial costs of sophisticated security solutions that do not cover important risks that are boring for IT. What should they invest in first? What are the basic things to guide us, even in the Big League? Paradoxically, even those who qualify for NIS2 still have problems with their list of priorities.
Somewhere in the 2000s, a group of security professionals under the umbrella of the SANS Institute (https://www.sans.org) began publishing what was known as the “SANS Top 20,” a list of actionable security controls based on analysis of prevalent attacks at the time. The list of controls has been continuously updated over the years based on observed trends, so that organizations prioritize implementing what works in practice, preventing the majority of attacks (85%). The initiative was later transferred to the Council on Cyber Security (CCS), and then to the Center for Internet Security (CIS) in 2015. Currently, the controls are known as the CIS 18 Framework (or CIS Critical Security Controls), and the current version is 8.1 (https://www.cisecurity.org/controls). There is also a version adapted for Industrial Control Systems (ICS) and Operating Technology (OT) (https://www.cisecurity.org/insights/white-papers/cis-critical-security-controls-v8-1-industrial-control-systems-ics-guide).
What is remarkable about CIS 18 is the organization of sub-controls (also called “safeguards” or measures) by priority, into implementation groups (Implementation Groups IG1, IG2, and IG3). Another remarkable aspect is the practical, prescriptive wording of the measures. Overall, most of them are also found in known security standards (https://www.cisecurity.org/cybersecurity-tools/mapping-compliance), except that standards do not specify where an organization should practically begin — this choice is left to the professionals. Last but not least, CIS 18 can be easily used for self-assessment — or a cybersecurity firm could compare the completed assessment (which can be associated with a maturity level) with those of other companies in the same industry. After all, the goal is not to have maximum security, but a better level than the competitors and one that is reasonable for the risks of the industry the organization belongs to (we don’t expect a retail chain to be as valuable a target as a bank).
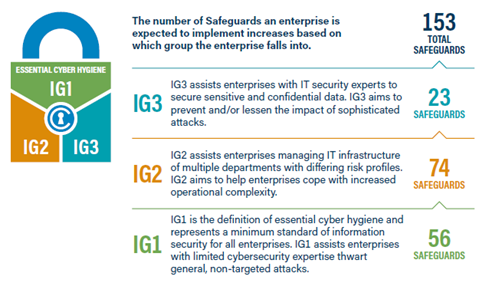
What should be reasonable for all companies, regardless of industry, are the measures that are part of IG1 (Implementation Group 1, “Essential Cyber Hygiene”), which should keep under control untargeted attacks (such as those that exploit accidental exposure). Only 3 out of the 18 controls do not have measures in IG1. Let’s list the 15 that do:
- 01 – Inventory and Control of Enterprise Assets
- 02 – Inventory and Control of Software Assets
- 03 – Data Protection
- 04 – Secure Configuration of Enterprise Assets and Software
- 05 – Account Management
- 06 – Access Control Management
- 07 – Continuous Vulnerability Management
- 08 – Audit Log Management
- 09 – Email and Web Browser Protections
- 10 – Malware Defenses
- 11 – Data Recovery
- 12 – Network Infrastructure Management
- 14 – Security Awareness and Skills Training
- 15 – Service Provider Management
- 17 – Incident Response Management
The order is not random. There are many organizations that haven’t even considered what needs to be protected (which assets and data are essential and how long they can be unavailable), or what should not be present, unnecessarily increasing the attack surface (for example, outdated software or a wireless access point brought from home by a user) — precisely the first three controls. Otherwise, organizations perform relatively well “on average,” but the maturity level can be misleading if seen as just an average.
Most organizations perform better when it comes to security solutions (10 – Malware Defenses) or perhaps account management (05 – Account Management), because security solution providers and SaaS vendors do their job well. But security is about the weakest link. There’s no point in implementing sophisticated measures in certain areas (let’s say 08 – Audit Log Management), even from IG2 or IG3 groups, if even one of the essential controls is completely ignored (such as 14 – Security Awareness and Skills Training).
Sometimes, measures from IG2 or IG3 are implemented before those from IG1. Let’s take, for example, 01 – Inventory and Control of Enterprise Assets. In this case, having a regular process for identifying and removing unauthorized devices is more important than purchasing an inventory software without doing anything with it.
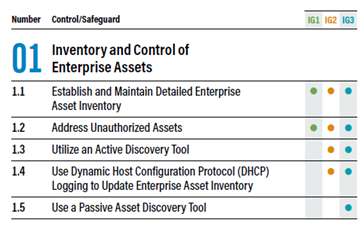
What does a security measure in CIS 18 look like in practice? Not very flexible, but rather strictly prescriptive:
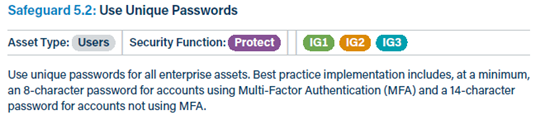
Lower flexibility can be a disadvantage for very large organizations (which tend to think more strategically than tactically), but for smaller organizations, there is no doubt about what would be considered good practice.
Regardless of the standards, some of the challenges organizations face are:
• Budget
• Lack of personnel with strong security skills. While IT staff may have solid security knowledge within their specific area of expertise, recommendations regarding the overall prioritization of measures may be entirely based on hearsay
• Choosing priorities, especially if NIS2 is not an obvious “choice”
Regardless of the standard used, Arctic Stream and its partner, Data Core Systems, can assess the security posture and ensure that security measures are implemented consistently and in a rigorous, logical order — not just as a compliance exercise (to meet legal requirements). For more information, you can contact us at [email protected].
For those who need to comply with NIS2, it and CIS 18 are complementary. NIS2 imposes stricter requirements for cybersecurity, training, and reporting, while CIS 18 provides a practical and detailed approach to implementing these requirements. NIS2 focuses on continuous risk assessment and incident management, which CIS 18 supports through specific controls for identifying, assessing, and mitigating risks, as well as establishing robust incident response plans. Additionally, NIS2 emphasizes supply chain security, and CIS18 includes controls for managing third-party risks, ensuring that vendors adhere to necessary security standards. By integrating CIS 18 into their security strategy, organizations can more easily meet NIS2 requirements while simultaneously building a stronger overall defense against cyber threats.